Operation Systems Theory: What are the fundamental concepts that underlie operating systems?
Operating systems (OS) control program execution, manage system resources for efficient operation, security measures, and employs error management. They coordinate software applications by interacting with hardware and users, which is crucial for executing programs and utilizing the system effectively. The hierarchical structure of operating systems reveals the relationships among subsystems, components, and subcomponents.
The user interface
acts as the bridge between the operating system and the user, offering
information and accepting commands. It can vary from graphical to command-line
interfaces. Networking involves processor interaction via communication lines,
either wired or wireless, and is vital for data exchange and collaborative
computing. Resource management includes the kernel, which provides fundamental
control over the computer, it oversees memory management and process management.
The kernel also connects to device management and I/O management, which control
hardware devices, drivers, and input/output operations respectively.
Operating systems
employ security measures to protect the software system and external devices. This
involves distinguishing between permitted commands and those not requiring
processing, enhancing overall system integrity. The OS also employs error
management, the system will receive errors, and then it will automatically work
to correct the errors. This is to help the operating system remain stable and
reliable.
Operating systems
enables processes to share and exchange information. A process is an
independent program in execution, consisting of the program code, data, and
execution context. It is the basic unit of execution in a computer system,
running independently with its own protected memory space. The process state
refers to the current condition of a process, which can be new, ready, running,
waiting, or terminated. The transition between these states is managed by the
operating system scheduler. The Process Control Block (PCB) is a data structure
used by the operating system to manage information about a process, including
the process state, program counter, registers, memory pointers, and other
execution details.
In a single-threaded
model, a process executes one sequence of instructions at a time, meaning if
one operation is blocked, the entire program is blocked. In contrast, a
multi-threaded model divides a process into multiple threads that execute
independently, sharing the same resources within the process for more
concurrent execution.
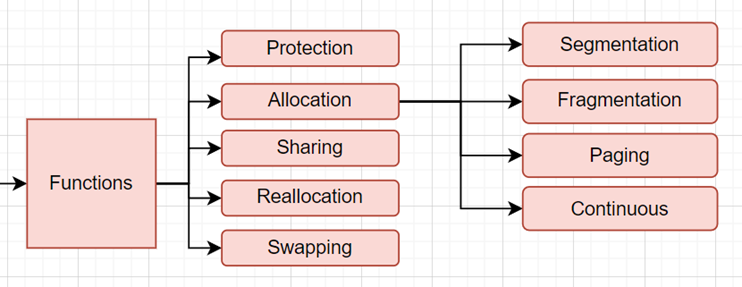
Memory management in
operating systems aims to optimize available memory resources by dynamically
allocating memory space to processes, ensuring each process receives what it
needs without wastage. The system also isolates processes and protects them
from unauthorized access. Memory management functions include: Protection,
allocation, reallocation, swapping, and sharing.
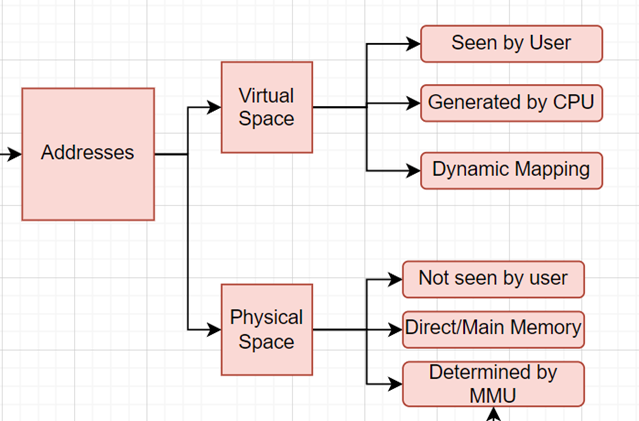
Distinct
characteristics emerge when considering physical and virtual address spaces.
Physical address space corresponds directly to hardware RAM, while virtual
address space represents a logical mapping used by processes, extending beyond
the physical limits of RAM into secondary storage. Virtual addresses require
translation to physical addresses, providing flexibility for dynamic allocation
and adjustment based on system needs.
File systems
management is crucial for organizing and safeguarding digital data. Its
objectives include data organization, ensuring data security through access
controls, efficient resource allocation, maintaining data availability, and
facilitating quick file access.
The functions of file
systems management are diverse, including file creation and deletion, directory
management, file reading and writing, permissions assignment, ensuring file
system integrity, backup, recovery, and file compression. Supported operations
within file systems management include reading, writing, appending, deleting,
renaming, copying, and moving files or directories.
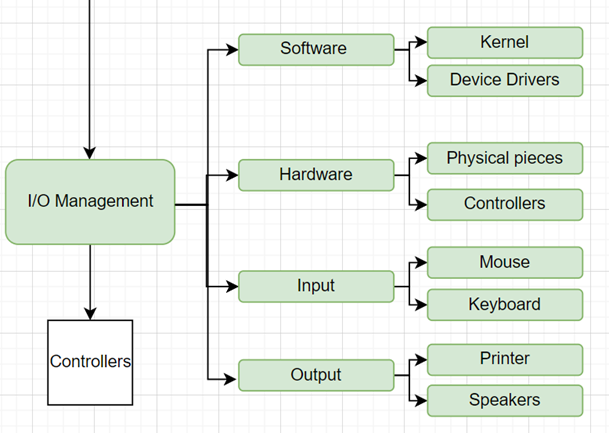
Input/output devices
includes various types, each serving a unique purpose in interacting with users
and computers. Some input devices include mouse and keyboard. Some output
devices include things such as printers and speakers. Network cards and modems
are also considered input/output devices.
The hardware layer
comprises the physical components of input/output devices, while the software
layer involves device drivers and interfaces that enable communication with
hardware. Integration across I/O and memory components is achieved through
memory-mapped I/O, buffering, caching mechanisms, interrupts, and DMA for
efficient data transfer without direct CPU involvement.
Domain-based
protection aims to confine processes within specific domains, restricting
access to resources within the designated domain. This enhances security by
preventing unauthorized access and limiting the level of trust among processes.
Language-based
protection refers to code that governs resource allocation. It enforces type
safety to prevent unintended memory access and data corruption, and implements
memory protection mechanisms to protect against memory-related vulnerabilities.
Encapsulation safeguards internal data structures from external interference.
The access matrix is a
table specifying each process’s permissions for each resource, serving as the
blueprint for access control mechanisms. The synergy between domain- and
language-based protection mechanisms, coupled with the utilization of access
matrices, forms the bedrock of a secure computer system. Using the matrix, the
protection component of the OS allows programs and users to only have access
that is defined by the computer system.
As
I look ahead to my future courses and jobs, I plan to incorporate key concepts
from operating systems theory in various ways. In System Design and
Architecture Courses, I aim to apply my understanding of contemporary operating
system features and structures. This will enable me to contribute to the design
and architecture of systems, focusing on optimizing resource management and
enhancing communication between system components.
In
Software Development, I intend to implement efficient inter-process
communication mechanisms based on my grasp of how operating systems facilitate
information exchange among processes. Additionally, I will design applications emphasizing
optimizing memory usage through considerations of main memory and virtual
memory management principles.
My
knowledge of file handling in modern computer systems, gained from Database
Management Courses, will play a role in contributing to the design of robust
database systems. I will also leverage my understanding of how the operating
system manages mass storage and I/O operations to improve overall database
performance. I see an opportunity to use my knowledge of access control
mechanisms to contribute to designing secure systems. This involves preventing
unauthorized access to resources and exploring how operating systems implement
security features to address cybersecurity threats. I aim to apply virtual
memory concepts to optimize resource utilization in cloud environments.
Additionally,
I will delve into how modern operating systems handle I/O operations,
contributing to the efficient design of virtualized environments. My
understanding of operating system structures will be used in troubleshooting
and optimizing system performance. I will also implement effective access
control mechanisms to ensure secure and compliant use of resources in practical
IT operations. By integrating these operating systems concepts into my
coursework and job responsibilities, I am excited to enhance my problem-solving
skills and contribute effectively to real-world challenges within the dynamic
field of computer science and IT.
Concept map final: https://drive.google.com/drive/folders/1L2eQ2EzLBydj7U123he_G09GBvJkofix?usp=sharing
Resources:
Curtis, B. (2023). Difference in
virtual address vs physical address. YourTechDiet. https://yourtechdiet.com/blogs/virtual-address-vs-physical-address-understanding-the-difference/
Hamilton, H. (n.d.). Solutions to the
critical section problem. https://www2.cs.uregina.ca/~hamilton/courses/330/notes/synchro/node3.html
Silberschatz, A., Galvin, P. B.,
& Gagne, G. (2014). Operating system concepts essentials (2nd ed.).
Retrieved from https://redshelf.com/







Comments
Post a Comment